[HV22.15] Message from Space
One of Santa’s elves is a bit of a drunkard and he is incredibly annoyed by the banning of beer from soccer stadiums. He is therefore involved in the “No Return to ZIro beer” community that pledges for unrestricted access to hop brew during soccer games. The topic is sensitive and thus communication needs to be top secret, so the community members use a special quantum military-grade encryption radio system.
Santa’s wish intel team is not only dedicated to analyzing terrestrial hand-written wishes but aims to continuously picking up signals and wishes from outer space too. By chance the team got notice of some secret radio communication. They notice that the protocol starts with a preamble. However, the intel team is keen to learn if the message is some sort of wish they should follow-up. Can you lend a hand?
Solution
We got a file ending in .cu8. Never heard of that before. Quick internet search leads to this github wiki entry from rtl_433, which suggests it has something to do with radio transmissions. Usual file analysis (binwal, strings) of the file message_1msps.cu8 doesn’t reveal anything useful, so let’s dig into the radio thing.
file message_1msps.cu8 returns RDI Acoustic Doppler Current Profiler (ADCP), which was quite a rabbit hole to dig into, but not a way towards the solution.
After trying out lots of tools, I ended up using URH / Universal Radio Hacker to open the file and play around with it. After simply opening it and zooming in, it shows a quite binary signal which looks promising.
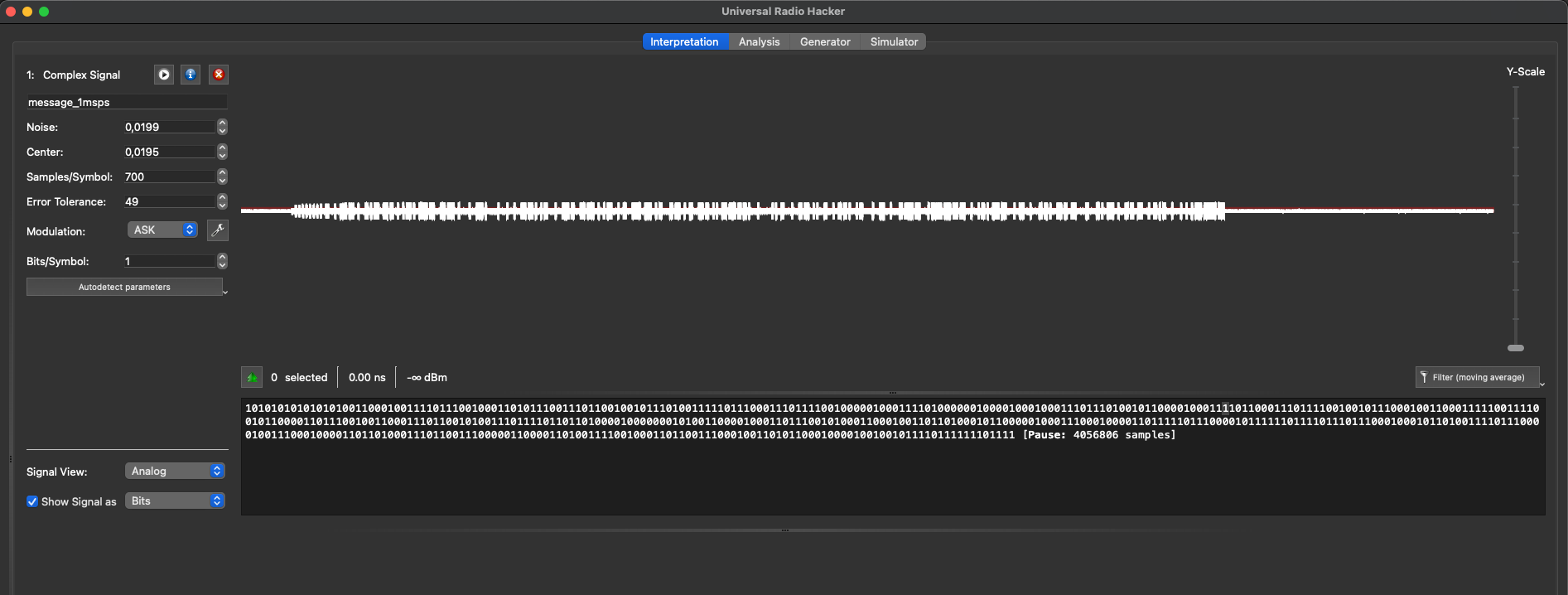
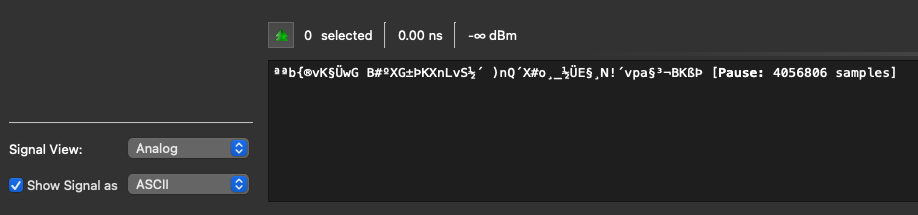
Selecting ascii as signal doesn’t show a flag, but that would be too easy, wouldn’t it?
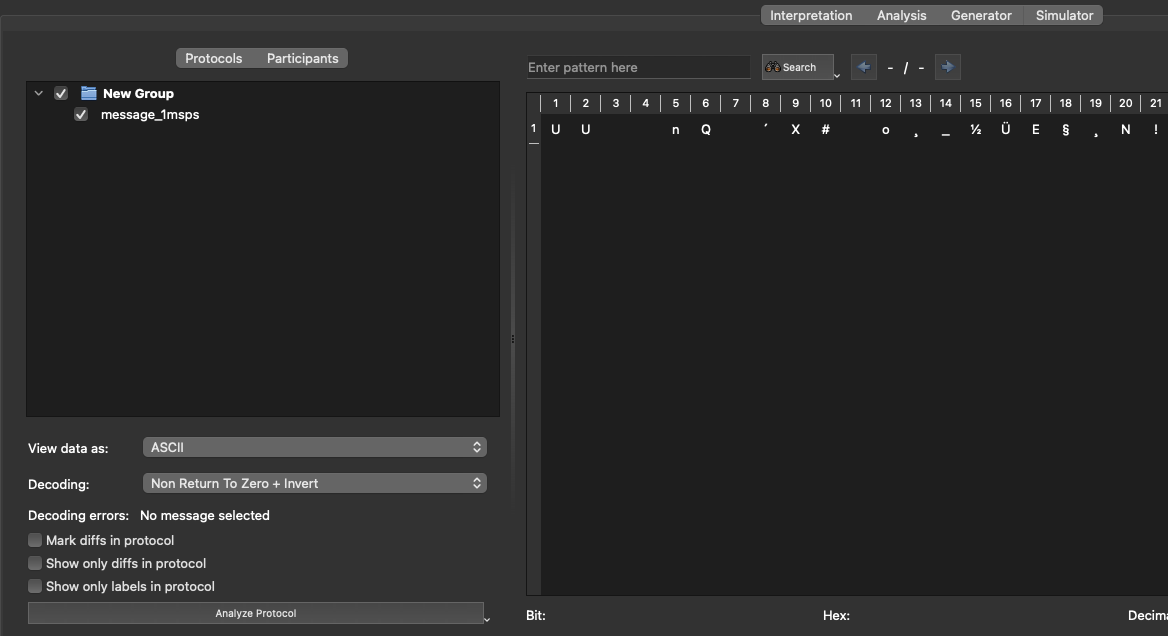
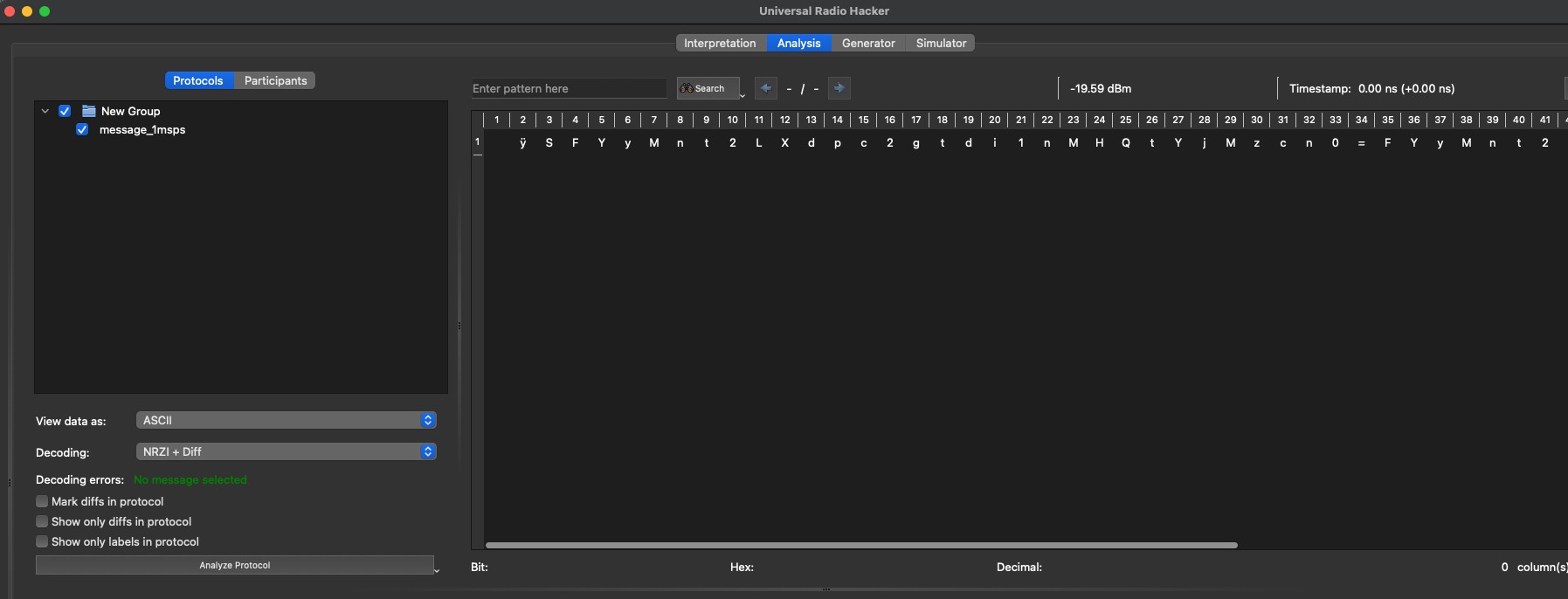
Going over to the analysis tab of the application, I notice there are some settings I can play around with. Looking through the options, Non Return seems familiar, since the bold expression in the challenge description is similar. If you take only the capital letters, it’s NRZI, which should be Non Return To Zero + Invert from the decoding. Unfortunately, this still doesn’t look like a flag, but feels closer:
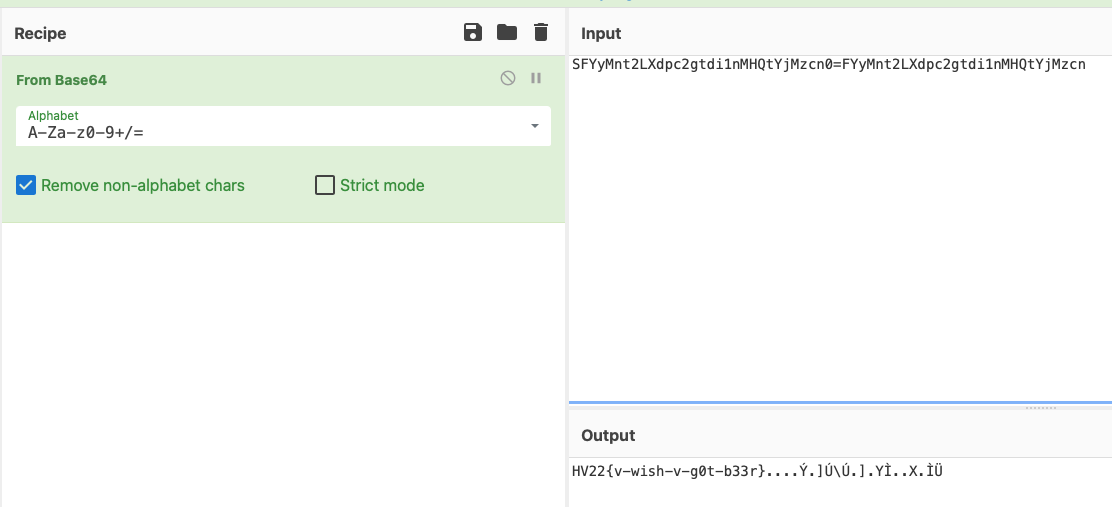
Playing around with the decoders (you can create your own by stacking functions), NRZI + Differential Encoding got me bytes like this. SFY seems familiar:
I just copied the bytes over to cyberchef and tried Base64 decode and voila, there is the flag HV22{v-wish-v-g0t-b33r}